
Hogan Lovells 2024 Election Impact and Congressional Outlook Report
 Search
Search


 Search
Search

The EU Cyber Resilience Act (CRA) (Regulation (EU) 2024/2847) is a pioneering piece of EU legislation that establishes mandatory cybersecurity standards for most hardware and software products made available on the EU market. The CRA enters into force on 10 December 2024 and leaves companies a period of three years to ensure that products with digital elements meet the CRA’s requirements in order to remain eligible for sale in the EU. Non-compliance with the CRA can lead to administrative orders and substantial fines. This article offers an overview on the CRA and recommended steps companies can take to ensure compliance.


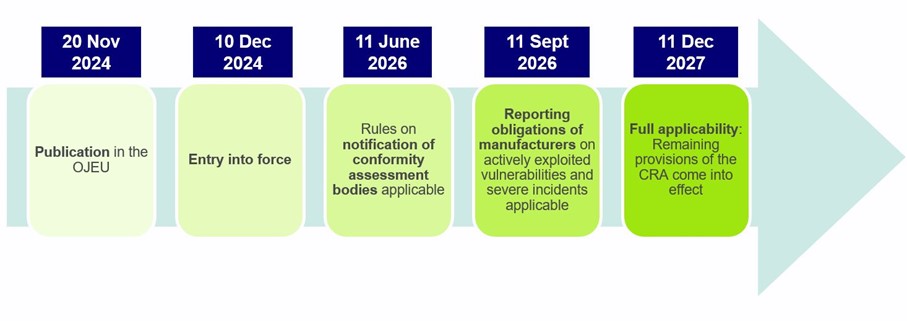
The CRA was adopted to address the growing popularity of digital products and increasing cybersecurity risks. After its publication in the EU Official Journal, the CRA will enter into force on 10 December 2024. Its overall applicability will commence after a three year period on 11 December 2027 (Art. 71 CRA), thereby giving companies time to implement the CRA requirements. Certain provisions on the notification of conformity assessment bodies will already apply from 11 June 2026. Also, manufacturers must comply with reporting obligations with regard to actively exploited vulnerabilities and severe incidents concerning their digital products from 11 September 2026.


The CRA’s material scope is very broad and generally includes all “products with digital elements” that are made available on the EU market, and whose “intended purpose or reasonably foreseeable use includes a direct or indirect logical or physical data connection to a device or network” (Art. 2(1) CRA). Such products with digital elements include all software or hardware products and their remote data processing solutions, including separately sold software or hardware components (Art. 3 no. 1 CRA).
The broad wording of this definition allows the CRA to cover a wide range of products, ranging from consumer products (e.g. IoT devices, B2C apps) to industrial systems. Cloud computing solutions can only be regarded as remote processing solutions to the extent they align with the criteria set forth under the CRA (see Art. 3 (2) CRA). Free and open-source software is only subject to the CRA to the extent it is intended for commercial activities (Recital (19) CRA).
In order for the CRA to be applicable, relevant products must be “made available on the market”. This encompasses supplying a product for distribution or use within the EU market during commercial activities, whether for payment or free of charge (Art. 3 (22) CRA; see Recital (15) CRA for further examples of commercial activities).
While the CRA’s objective is to set extensive cybersecurity standards for products with digital elements made available on the EU market, it allows for exceptions for specific products (Art. 2(2)-(8) CRA): Products that are subject to specific EU regulations, spare parts, products developed or modified exclusively for national security or defence purposes and products specifically designed to process classified information.
The CRA addresses various “economic operators” along the supply chain, including manufacturers, authorized representatives, importers and distributors (Art. 3 (12) CRA). Further, it stipulates a separate set of obligations that applies to open-source software (OSS) stewards (Art. 3 (14) CRA).
With regard to the territorial scope of the CRA, the marketplace principle applies and the regulatory framework encompasses all products with digital elements made available on the EU market (Art. 2(1), 3 (22) CRA). In consequence, the CRA has implications for economic operators within and outside the EU, if they make products with digital elements available on the EU market or seek to significantly modify products already made available on the EU market once the CRA is in effect.


The set of CRA obligations applicable to a product with digital elements depends on the cybersecurity risk level associated with the product category. In particular, the CRA differentiates between critical, important (class I and II), and non-critical products, whereby the latter are estimated to account for 90% of products on the EU market.
|
Product category |
Description and Relevant Provisions |
Examples (non-exhaustive) |
|
Non-critical ~ 90% of products |
General requirements (Art. 6 CRA) |
Photo editing software, text processing software, hard drives, games, smart home products without security functions |
|
Important (class I) |
Core functionality of one of the product categories listed in Annex III CRA 1.Either primarily performs functions that are critical to the cybersecurity of other products, networks or services, or 2.performs a function that carries a significant risk of adverse effects with regard to its intensity and ability to disrupt, control or cause damage to (i) a large number of products, or (ii) the health, security or safety of its users through direct manipulation (Art. 7(2) CRA) General + additional requirements (Art. 6 and 7 CRA) |
Identity management systems and hardware, browsers, password managers, network management systems, operating systems, routers and modems, public key infrastructure, smart home products with security functions (Annex III CRA) |
|
Important (class II) |
Core functionality of one of the product categories listed in Annex III CRA Same criteria as class I (Art. 7(2) CRA) General + additional requirements (Art. 6 and 7 CRA) |
Container or virtual machines, firewalls, intrusion detection and prevention systems, tamper-resistant microprocessors and microcontrollers (Annex III CRA) |
|
Critical |
Core functionality of one of the product categories listed in Annex IV CRA 1.Either critical dependency of essential entities pursuant to Art. 3 NIS2 Directive on the product category, or 2.the potential of serious disruptions to critical supply chains across the EU market as a result of incidents and exploited vulnerabilities concerning the product category (Art. 8(2) CRA, Recital (46) CRA). General + additional requirements (Art. 6 and 8 CRA) |
Hardware devices with security boxes, smart meter gateways within smart metering systems and other devices for advanced security purposes, including for secure cryptoprocessing, smartcards or similar devices, including secure elements (Annex IV CRA) |


The CRA establishes a comprehensive framework of cybersecurity obligations on economic operators involved in the supply chain of products with digital elements, even imposing a distinct set of obligations on OSS stewards.


A crucial part of the obligations of the manufacturer set out by the CRA is the performance of the conformity assessment (Art. 13(12), 32 CRA). This is the process of verifying whether the essential cybersecurity requirements set out in Annex I have been fulfilled (Art. 3 (27) CRA). First, it is necessary for manufacturers to identify products with digital elements and then classify these products in the beforementioned product categories, as different procedures apply to the distinct product classes. The CRA mainly distinguishes between internal and external procedures.
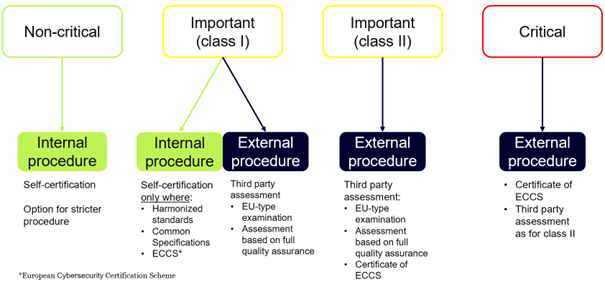
After successfully performing the relevant conformity assessment procedure, the manufacturer is obliged to draw up the EU declaration of conformity (Art. 28 CRA) and affix the Conformité Européenne CE-marking (Art. 29, 30 CRA).


It is likely that the majority of companies involved in the production and distribution of hardware or software products on the EU market will be affected by the CRA in some way. Therefore, it is advisable to take the necessary steps to ensure compliance with the CRA.
Even though most of the obligations imposed by the CRA will not come into full effect until 11 December 2027, it is still recommended that companies commence CRA compliance projects as soon as possible. This applies in particular in light of product development and release timelines, given that the requirements of the CRA will impact these stages of the product lifecycle significantly.
In order to ensure CRA compliance, companies could take the following practical steps:
Companies should consider their individual situation to further specify the relevant steps required to comply with the CRA and should keep a close eye on the ongoing legal developments related to the CRA, including the development and adoption of harmonized standards as well as the appointment of responsible notified conformity assessment bodies.
Authored by Dr. Henrik Hanssen and Anna Theresa Vogel.